-
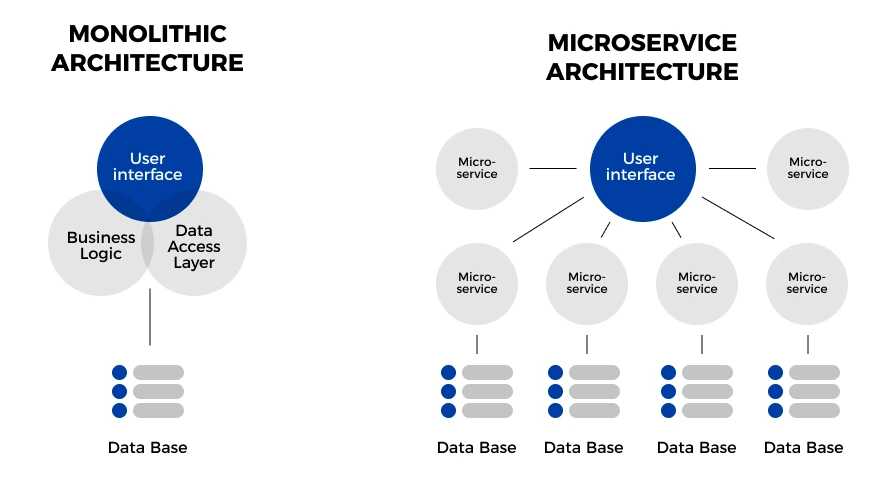
Microservices vs. Monolithic Architecture: Unraveling the Key Differences
In the world of software architecture, two predominant approaches emerge: microservices and monolithic. These architectures represent fundamentally different ways of designing and developing software systems. Let’s delve into the concepts of microservices and monolithic architecture, and then explore the key differences between them. Microservices Architecture: Definition: Microservices is an architectural style where an application is…
-
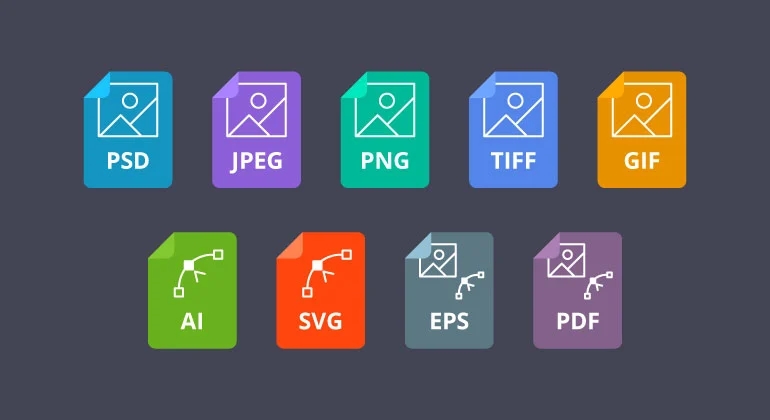
Brief Understanding File Types
2. Document File Types 3. Image File Types 4. Audio File Types 5. Video File Types 6. Compressed File Types 7. Executable File Types 8. Web File Types 9. Database File Types 10. Miscellaneous File Types 11. Font Files 12. Video Game File Types 13. 3D Model File Types 14. CAD File Types 15. GIS…
-

Understanding IP Addresses and the Difference Between IPv4 and IPv6
An IP address, short for Internet Protocol address, is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It serves as a unique identifier for devices, allowing them to send and receive data within a network and across the internet. IPv4 (Internet Protocol version 4):…
-
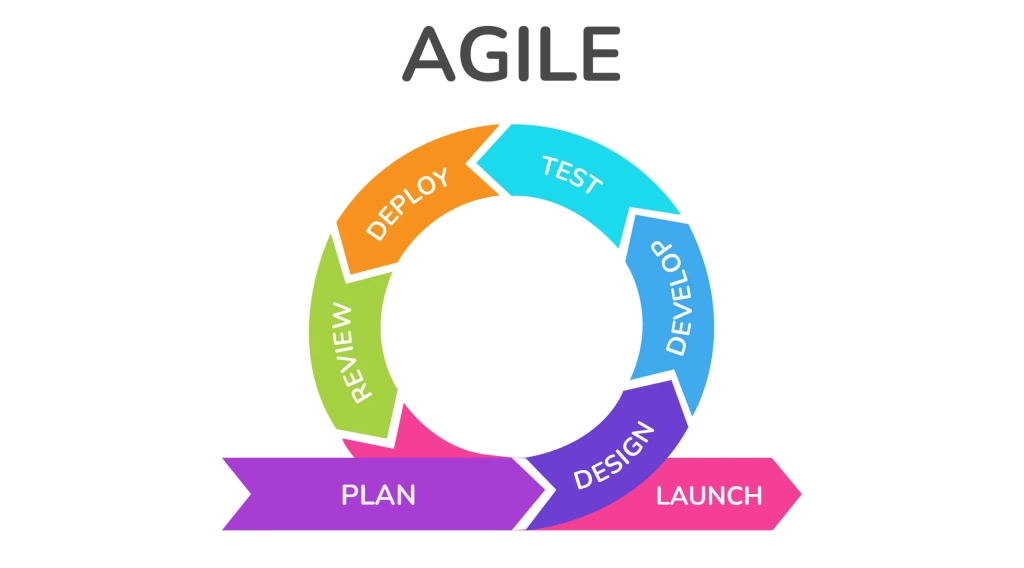
Demystifying Agile Methodology
Agile methodology is a flexible and collaborative approach to project management that has revolutionized how teams work, particularly in the software industry. Born out of the need to respond to changing requirements and deliver value quickly, agile has become a cornerstone of modern project management. Let’s break down the key aspects of agile, its origins,…
-

Comprehensive Guide to Test Management: Software Testing, Test Cases, Test Plans, and Test Automation
In the ever-evolving landscape of software development, the pursuit of excellence in quality and performance is a constant endeavor. Central to this pursuit is test management, a fundamental process that ensures the effectiveness, reliability, and user satisfaction of software products. This comprehensive guide delves into the intricacies of test management, providing an in-depth exploration of…
-
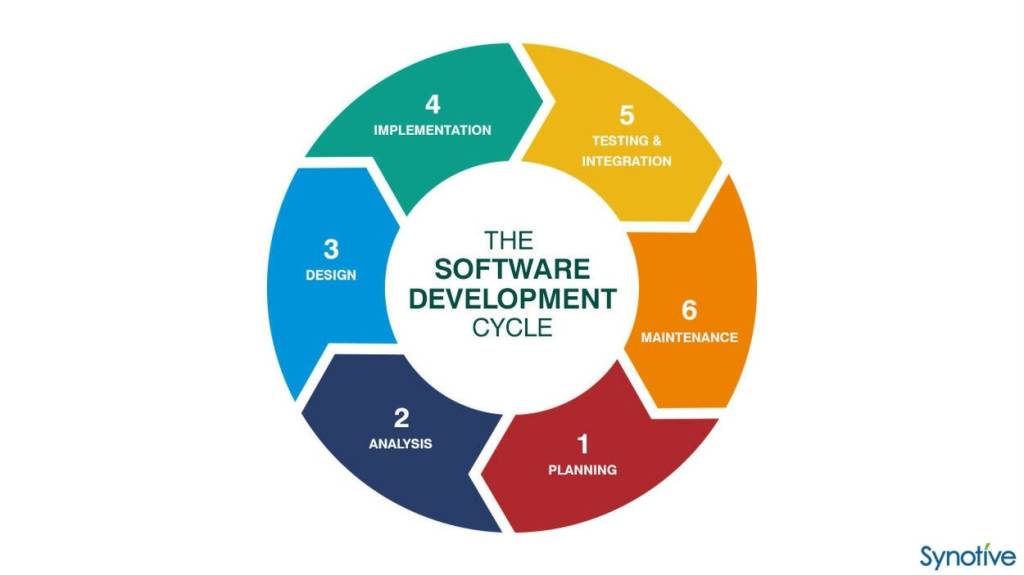
Exploring the Software Development Life Cycle (SDLC): Phases, Methodologies, and Benefits
The Software Development Life Cycle (SDLC) is a systematic process that outlines the phases, tasks, and activities involved in designing, developing, testing, deploying, and maintaining software applications or systems. It serves as a structured framework to ensure that software projects are planned, executed, and completed in an organized and efficient manner. SDLC provides a roadmap…
-

Review Figma Tool
What is Figma? Figma is a collaborative web application tailored for interface design, complemented by offline functionality through desktop applications for both macOS and Windows platforms. This comprehensive platform is dedicated to user interface and user experience (UI/UX) design, highlighting real-time collaboration. It offers an array of tools encompassing vector graphics editing and prototyping capabilities.…
-

Review About Futurepedia 10 AI Tools
Introduction The rapid advancements in artificial intelligence have brought forth a plethora of innovative AI tools that cater to various needs in different industries. These AI tools have revolutionized the way we work and interact with technology. Among the diverse range of AI tools available, one platform that stands out is Futurepedia10. Futurepedia10 serves as…
-

Follow These 8 Rules to Keep Hackers Away from Your Passwords
Introduction: In today’s digital age, online security is of utmost importance. With cyber threats and hacking attempts becoming increasingly sophisticated, protecting your passwords has become a critical aspect of safeguarding your personal and sensitive information. By following a few essential rules, you can significantly enhance the security of your passwords and reduce the risk of…
-

APIs Unraveled: Understanding Application Programming Interfaces
Imagine you are in a big amusement park, and you want to play a game at a booth to win a prize. However, you cannot directly go to the booth and play the game yourself because there’s a safety barrier between you and the booth. Instead, you need to hand over some tokens to a…
